Crowdstrike update causes major issues around the world
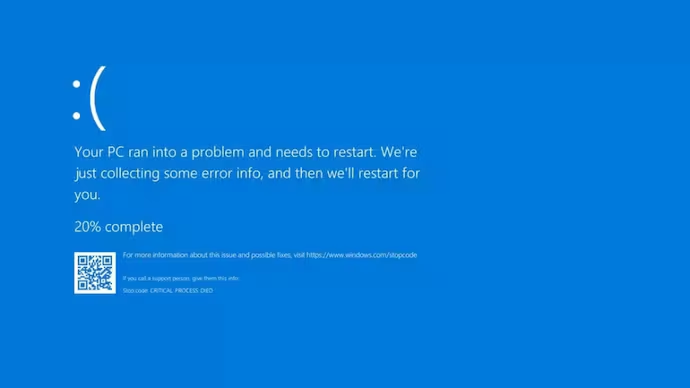
CrowdStrike Update Pushing Windows Machines Into a BSOD Loop.
Crowdstrike, a cybersecurity technology company that provides endpoint security, threat assessment and cyberattack response services, served up a very unfortunate update to Microsoft’s Windows 10 and 11 ecosystem. A recent update to the company´s Falcon sensor is causing major issues for Microsoft Windows users worldwide. This update is leading to blue screen of death (BSOD) loops and making systems inoperable.
The bottom line is that airports, banks, online websites, healthcare and the media (incl. traditional TV), to name a few, are struggling because the update created so much havoc that affected machines ended up with a complete stop in the form of the familiar BSOD / blue screen. Many flights have been grounded, with queues and delays at airports, while shops and communications have also been hit.
Microsoft has said it is taking “mitigation action” to deal with “the lingering impact” of the outage.
The issue, which began on July 19, 2024, affects Windows 10 and 11 systems running CrowdStrike’s endpoint security software. Users report experiencing repeated BSODs with the error message “DRIVER_OVERRAN_STACK_BUFFER,” which prevents normal system boot and operation.
More specifically, it is the Falcon Sensor software that is to blame for all the problems. The program is described by Crowdstrike as “blocking attacks on your systems while capturing and recording activity as it happens to detect threats quickly.”
Just before 12:00 CST+1, their CEO George Kurtz stepped out in a message on X, where he writes that the company is “actively working to find solutions”. He points to an error for Windows users and says that the problems do not affect Mac or Linux.
Statement on Windows Sensor Update
CrowdStrike is actively working with customers impacted by a defect found in a single content update for Windows hosts. Mac and Linux hosts are not impacted. This is not a security incident or cyberattack.
The issue has been identified, isolated and a fix has been deployed. We refer customers to the support portal for the latest updates and will continue to provide complete and continuous updates on our website.
We further recommend organizations ensure they’re communicating with CrowdStrike representatives through official channels.
Our team is fully mobilized to ensure the security and stability of CrowdStrike customers.
The data problems first reported in Australia are related to a security update.
Crowdstrike is reporting that they have fixed the bug with the updates Computer security company Crowdstrike reports that the problem that caused global IT problems on Friday has been identified and isolated, and a fix has been implemented.
The serious IT problems affect many large international companies, including airports, banks and websites worldwide. The problems also affect a number of Norwegian businesses.
The incident is referred to as the biggest IT collapse in history.
How to Check CrowdStrike sensor version is affected by the BSOD issue
- Identify your sensor version:
Boot into Safe Mode and check the CrowdStrike Falcon sensor version installed on your system. The problematic update seems to be affecting various sensor versions, including version 6.58. - Check the installation date:
Look at the installation date of the CrowdStrike Falcon sensor. If it coincides with the onset of BSOD issues (around July 19, 2024), it’s likely to be the cause. - Look for specific error messages:
The BSOD error associated with this issue is “DRIVER_OVERRAN_STACK_BUFFER”. If you’re seeing this error, your system is likely affected.
How to fix the Crowdstrike bug (Possible Workarounds)
- Start Windows in Safe Mode or open the Windows Recovery Environment
- Navigate to C:\Windows\System32\drivers\CrowdStrike
- Find the file “C-00000291*.sys” and delete it
- Restart the machine
And according to those in the know, the fix will probably have to be applied separately to each and every device affected – causing a massive headache for IT departments everywhere around the world.
